Rumored Buzz on Ipvanish Vs Nordvpn
Table of ContentsThe 7-Second Trick For Ipvanish Vs NordvpnThe 3-Minute Rule for Ipvanish Vs Nordvpn
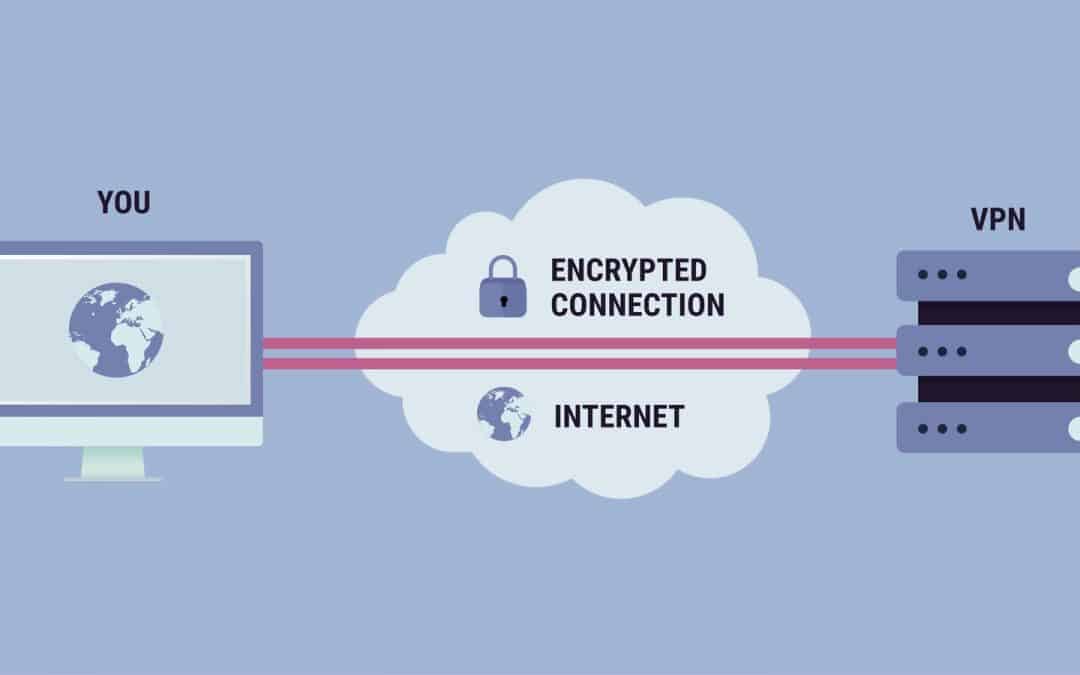
Its style meets most security goals: schedule, stability, and privacy - ipvanish vs nordvpn.IPsec utilizes encryption, encapsulating an IP packet inside an IPsec packet. De-encapsulation occurs at the end of the tunnel, where the original IP package is decrypted and forwarded to its desired destination. Transport Layer Security( SSL/TLS) can tunnel a whole network's traffic (as it carries out in the OpenVPN project and SoftEther VPN job) or protect an individual connection. An SSL VPN can link from areas where IPsec runs into difficulty with Network Address Translation and firewall program guidelines.
Datagram Transportation Layer Security( DTLS) utilized in Cisco AnyConnect VPN and in OpenConnect VPN to fix the problems SSL/TLS has with tunneling over TCP( tunneling TCP over TCP can lead to big hold-ups and connection terminates ). Microsoft Secure Socket Tunneling Procedure (SSTP) tunnels Point-to-Point Procedure (PPP) or Layer 2 Tunneling Protocol traffic through an SSL/TLS channel( SSTP was presented in Windows.
Server 2008 and in Windows Vista Service Load 1). Multi Path Virtual Private Network( MPVPN). Ragula Systems Advancement Business owns the signed up hallmark" MPVPN". Protected Shell( SSH) VPN OpenSSH deals VPN tunneling( unique from port forwarding) to protect remote connections to a network or to inter-network links. The VPN function itself does not support personal authentication. WireGuard is a procedure. In 2020, WireGuard assistance was contributed to both the Linux and Android kernels, opening it as much as adoption byVPN providers. By default, WireGuard makes use of Curve25519 for essential exchange and ChaCha20 for file encryption, but likewise consists of the capability to pre-share a symmetric key in between the customer and server. User-created remote-access VPNs may use passwords, biometrics, two-factor authentication or other cryptographic methods. Network-to-network tunnels typically use passwords or digital certificates. They completely save the key to permit the tunnel to develop instantly, without intervention from the administrator. Tunneling protocols can run in a point-to-point network topologythat would in theory not be considered a VPN because a VPN by definition is anticipated to support arbitrary and altering sets of network nodes. Site-to-Site VPN terminology. Depending on whether a provider-provisioned VPN( PPVPN) runs in layer 2 or layer 3, the building obstructs explained listed below might be L2 just, L3 only, or a combination of both. Multi-protocol label switching (MPLS) performance blurs the L2-L3 identity. [.
] 4026 generalized the following terms to cover L2 MPLS VPNs and L3 (BGP) VPNs, but they were presented in 2547. C gadgets are not knowledgeable about the VPN. Consumer Edge device (CE) A gadget at the edge of Bonuses the consumer's network which offers access to the PPVPN. Often it is simply a demarcation point between provider and consumer duty. Other companies enable clients to configure it. Provider edge device (PE) A gadget, or set of devices, at the edge of the company network which links to client networks through CE gadgets and provides the supplier's view of the consumer site. Provider gadget (P) A gadget that operates inside the service provider's core network and does not straight user interface to any consumer endpoint. It might, for instance, offer routing for many provider-operated tunnels that come from different consumers' PPVPNs. While the P gadget is an essential part of implementing PPVPNs, it is not itself VPN-aware and does not keep VPN state. P-to-P connections, in such a function, often are high-capacity optical links in between major places of suppliers. Virtual LAN Virtual LAN( VLAN) you can look here is a Layer 2 strategy that permit the coexistence of several regional area network( LAN) broadcast domains interconnected by means of trunks utilizing the IEEE 802. 1Q trunking protocol. Other trunking procedures have actually been used but have ended up being outdated, consisting of Inter-Switch Link( ISL ), IEEE 802.
What Does Ipvanish Vs Nordvpn Do?
EtherIP has just packet encapsulation mechanism. It has no confidentiality nor message stability defense. EtherIP was presented in the FreeBSD network stack and the SoftEther VPN server program. IP-only LAN-like service (IPLS) A subset more tips here of VPLS, the CE gadgets need to have Layer 3 abilities; the IPLS presents packets rather than frames.
This section talks about the main architectures for PPVPNs, one where the PE disambiguates duplicate addresses in a single routing circumstances, and the other, virtual router, in which the PE consists of a virtual router circumstances per VPN. The former technique, and its versions, have actually gained the most attention. Among the obstacles of PPVPNs involves various customers utilizing the exact same address space, particularly the IPv4 private address area.

BGP/MPLS PPVPN In the approach specified by 2547, BGP extensions market paths in the IPv4 VPN address family, which are of the kind of 12-byte strings, starting with an 8-byte route distinguisher (RD) and ending with a 4-byte IPv4 address. RDs disambiguate otherwise replicate addresses in the very same PE - ipvanish vs nordvpn. PEs understand the topology of each VPN, which are interconnected with MPLS tunnels either straight or through P routers.